|
|
Troubleshooting TCP/IP Connectivity
This chapter presents protocol-related troubleshooting information for Transmission Control Protocol/Internet Protocol (TCP/IP) connectivity problems. The chapter consists of the following sections:
Each symptom module is divided into the following sections:
TCP/IP Route Redistribution and Access Control Scenario
Many of the largest internetworks employ TCP/IP as their backbone network protocol. However, this does not mean that these networks employ universal internetworking implementations. In fact, TCP/IP internetworks---sometimes comprising thousands of internetworking nodes---can span organizational domains that employ completely different topologies, routing protocols, and possibly conflicting administrative objectives. The challenge is to provide the requisite level of connectivity between hosts in different domains and on different major networks, while providing adequate security for each organization attached to the internetwork. This scenario focuses on the issue of balancing connectivity and security.
This scenario addresses connectivity problems in TCP/IP internetworks. Figure 11-1 illustrates interconnections from one subnet to a corporate network as well as interconnections to external networks.
Figure 11-1 : TCP/IP Internetwork Connectivity Scenario Map
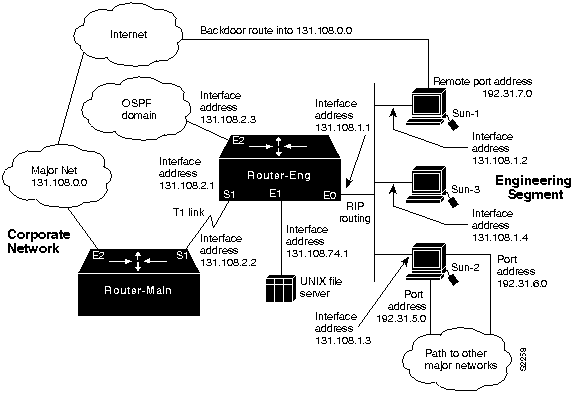
Sun-1, Sun-2, and Sun-3 on the Ethernet segment attached to Router-Eng are unable to communicate with hosts in the main corporate network or outside the organization through Router-Eng. Several backdoor routes also exist, which allow other networks to access the engineering segment.
Because external access is not being reliably controlled and because users on the engineering segment are unable to get through to the corporate network via Router-Eng, this scenario represents a security problem as well as a connectivity problem.
The relevant elements of the internetworking environment shown in Figure 11-1 can be summarized as follows:
Diagnosing and Isolating Problem Causes
Given the situation, the following candidates are likely causes for interconnection problems:
The next step is to analyze each potential cause as the problem source and then test the network to determine whether it is operational after each modification is made. The following discussion considers these possible problems and alternatives for providing the proper access and security.
Isolating Router Software Configuration Problems
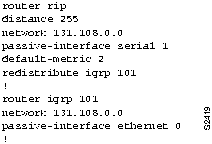
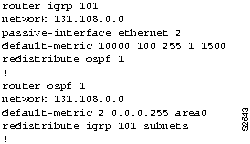
Because the UNIX workstation-based routers on the engineering segment are using RIP to route among themselves, while the corporate network uses IGRP, the first configuration issue to consider is route redistribution.
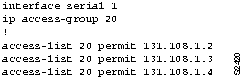
Figure 11-2 : RIP-to-IGRP Route Redistribution Configuration Example Figure 11-3 : IGRP-to-OSPF Route Redistribution Configuration Example Figure 11-4 : Access Control Additions to Router-Eng Configuration Figure 11-5 : Standard Access Control for Router-Eng Configuration Figure 11-6 : Extended Access Control for Router-Eng Configuration This scenario focused on solving two problems in TCP/IP internetworks:
Of these two, implementing redistribution is relatively straightforward, while access lists can be fairly complicated and can yield unexpected results.
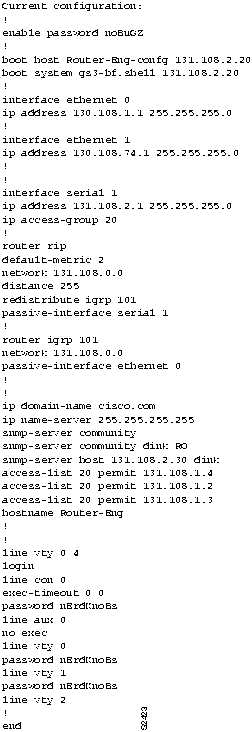
Figure 11-7 illustrates a complete router configuration for Router-Eng (obtained by using the write terminal privileged EXEC command).
Figure 11-7 : Complete Example Configuration for Router-Eng The symptom modules in the following sections pertain to TCP/IP internetwork problems. Unless otherwise indicated, each module is presented as a set of general problems. Where there are special considerations associated with a situation, notes are included.
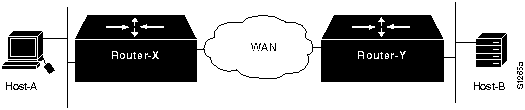
Host Cannot Access Offnet Hosts
Symptom: Host-A is unable to communicate with Host-B on another network. When you attempt to make a connection to an intervening router, you may or may not be able to make a successful connection. For example, you can ping Router-X but not Router-Y. In either case, you are unable to connect to the target host on the other side of the router. This situation is illustrated in Figure 11-8.
Figure 11-8 : Host-A Cannot Communicate with Host-B over Routers Table 11-1 outlines possible causes and suggested actions when a host cannot access offnet hosts.
Table 11-1 : TCP/IP: Host Cannot Access Offnet Hosts
Host Cannot Access Certain Networks
Symptom: Host cannot access certain networks on the other side of a router. Some networks might be accessible. Table 11-2 outlines possible causes and suggested actions when a host cannot access certain networks.
Table 11-2 : TCP/IP: Host Cannot Access Certain Networks
Connectivity Available to Some Hosts but Not Others
Symptom: Hosts on a network can communicate with specific hosts on the other side of a router, but are unable to communicate with certain other hosts. Table 11-3 outlines possible causes and suggested actions when connectivity is not available to all hosts.
Table 11-3 : TCP/IP: Connectivity Not Available to all Hosts
Some Services Are Available, Others Are Not
Symptom: In some cases, you might be able to get through to hosts using some protocols, but cannot get through using others. For instance, you might be able to ping a host and FTP to a host, but Telnet does not get through. Table 11-4 outlines a possible cause and suggested actions when not all services are available.
Table 11-4 : TCP/IP: Not All Services Are Available
For information on how to create access-lists, refer to the Router Products Configuration Guide.
Users Cannot Make Connections when One Parallel Path Is Down
Symptom: In configurations that feature multiple paths between networks, there is no communication over the alternative routes when one of the parallel links breaks.
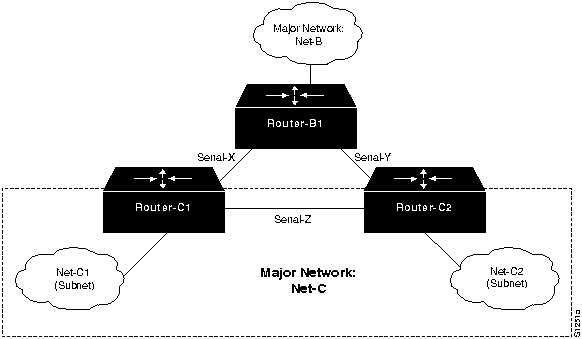
Figure 11-9 illustrates one example of a situation in which this lack of communication can occur. Here, one major network (Net-B) has two or more access points into another major network (Net-C), while a third link joins two separate subnets of Net-C. Details are provided in Table 11-5.
Figure 11-9 : Problem Parallel Path Topology Example Table 11-5 outlines possible causes and suggested actions when users cannot make connections when one parallel path is down.
Table 11-5 : TCP/IP: Users Cannot Make Connections when One Parallel Path Is Down
Router Sees Duplicate Routing Updates and Packets
Symptom: Router sees duplicate routing updates on different interfaces. Network users might experience sudden loss of connections and extremely poor performance. Router sees other routers and hosts on multiple interfaces. Table 11-6 outlines a possible cause and suggested actions when a router sees duplicate routing updates and packets.
Table 11-6 : TCP/IP: Router Sees Duplicate Routing Updates and Packets
Routing Works for Some Protocols, Not for Others
Symptom: Some protocols are routed, others are not. Telnet, for example, works from a host on one network to a host on another network on the other side of a router, but FTP does not. Perhaps Domain Name Service (DNS) works with your own domain, but does not work for external domains. Table 11-7 outlines a possible cause and suggested actions when routing does not work for all protocols.
Table 11-7 : TCP/IP: Routing Does Not Work for All Protocols
Router or Host Cannot Reach Nodes on the Same Network
Symptom: A router or host is unable to communicate with other routers or hosts known to be connected to the same network. Table 11-8 outlines possible causes and suggested actions when a router or host cannot reach nodes on the same network.
Table 11-8 : TCP/IP: Router or Host Cannot Reach Nodes on the Same Network
Note about IP Addresses and Subnet Masks
In most IP networks, routers and hosts should agree on their common subnet mask. If a router and a host disagree on the length of the subnet mask, packets might not be routed correctly. Consider the situation described in Table 11-9.
A host interprets a particular address (192.31.7.49) as being Host 1 on the third subnet (subnet address 48). However, because it is using a different subnet mask, the router interprets the address as belonging to Host 17 on the first subnet (subnet address 32). Depending on its configuration, the router drops any packet destined for 192.31.7.49 or sends it out on the wrong interface.
Table 11-9 : Comparison of Host and Router Subnet Mask Effects
OSPF Networks Are Not Advertised
Symptom: OSPF routes and networks are not being advertised to other routers. Routes are not in the routing table, and hosts are unable to communicate. Table 11-10 lists a possible cause and suggested actions when OSPF networks are not being advertised.
Table 11-10 : TCP/IP: OSPF Networks Are Not Advertised
OSPF Routers Do Not Communicate
Symptom: Connectivity fails for OSPF routers and networks. Hosts or routers do not communicate with one another. Table 11-11 lists possible causes and suggested actions for OSPF routers that do not communicate.
Table 11-11 : TCP/IP: OSPF Routers Do Not Communicate
OSPF Protocols Fail to Work on New Interfaces
Symptom: New interfaces are added to a router, but the protocol configured for the router does not work on the new interfaces. New interfaces in the router are assigned to a different major network than existing interfaces, and the routing protocol fails. Table 11-12 lists a possible cause and suggested actions when OSPF routing protocols fail to work on new interfaces.
Table 11-12 : TCP/IP: OSPF Protocols Fail to Work on New Interfaces
OSPF Routers Are Not Receiving Routing Information from Other Areas
Symptom: OSPF nodes in one area are not seeing routing information for other areas. Some hosts being are unable to communicate with hosts in other areas, and routing table information is incomplete. Table 11-13 lists possible causes and suggested actions when OSPF routers are not receiving routing information from other areas.
Table 11-13 : TCP/IP: OSPF Routers Not Receiving Routing Information from Other Areas
Figure 11-10 : Virtual Links and Transit Areas OSPF Routers Are Not Communicating Dynamically
Symptom: OSPF routers are not communicating dynamically with their neighbors. Some routers can communicate, but some routers are unreachable. Table 11-14 lists possible causes and suggested actions when OSPF routers are not communicating dynamically.
Table 11-14 : TCP/IP: OSPF Routers Not Communicating Dynamically
OSPF External Routes Incorrectly Advertised into Stub Area
Symptom: OSPF external routes are incorrectly advertised into a stub area. Some routers can communicate, but specific routers or hosts are unreachable. Table 11-15 lists a possible cause and suggested actions when OSPF external routes are incorrectly advertised into a stub area.
Table 11-15 : TCP/IP: OSPF External Routes Incorrectly Advertised into Stub Area
IGRP Routers Do Not Communicate
Symptom: Connectivity fails for IGRP routers and networks. Hosts or routers do not communicate with one another. Table 11-16 lists possible causes and suggested actions when IGRP routers are not communicating.
Table 11-16 : TCP/IP: IGRP Routers Not Communicating
Traffic Is Not Getting through Router Using Redistribution
Symptom: Traffic is not getting through a router that is redistributing routes between two different routing domains---typically RIP and IGRP. Observed symptoms range from poor performance to no communication at all. Poor performance can occur when nonoptimal routes are used because the best path is blocked by a misconfigured redistribution. Table 11-17 outlines possible causes and suggested actions when traffic is not getting through a router using route redistribution.
Table 11-17 : TCP/IP: Traffic Not Getting through Router Using Redistribution
IGRP or RIP Fail to Work on New Interfaces
Symptom: New interfaces are added to a router, but the protocol configured for the router does not work on them. The new interfaces are assigned to a different major network than existing interfaces, and the routing protocol fails. Table 11-18 lists a possible cause and suggested actions when IGRP or RIP fail to work on new interfaces.
Table 11-18 : TCP/IP: IGRP or RIP Fail on New Interfaces
Redistribution route-map Commands Behave Unexpectedly
Symptom: A series of redistribute and route-map router configuration commands allow some routes to be redistributed but deny others. Also, some routes that are configured to deny redistribution are redistributed. Table 11-19 lists possible causes and suggested actions when redistribution problems occur with the redistribute and route-map router configuration commands.
Table 11-19 : TCP/IP: Redistribution route-map Commands Behave Unexpectedly
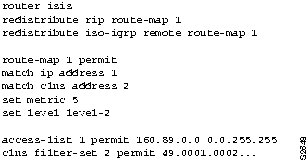
Consider the example configuration shown in Figure 11-11 and the modified configuration shown in Figure 11-12. In Figure 11-11, a router is configured to redistribute RIP and ISO-IGRP routes into an Intermediate System-to-Intermediate System (IS-IS) level-2 LSP with a metric of 5. All destinations on the RIP network with address 160.89.0.0 are redistributed, as are all ISO-IGRP routes with a prefix of 49.0001.0002.
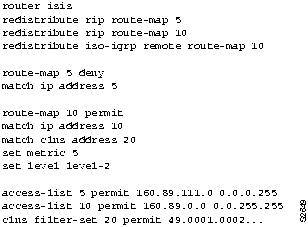
Figure 11-11 : Configuration Example for Redistribution Using Route Maps However, you want to exclude a particular subnet from RIP route redistribution. The additional configuration commands shown in Figure 11-12 exclude subnet 160.89.111.0. By assigning a sequence number of 5, you ensure that this address will be excluded before the more general access for 160.89.0.0 is processed. The redistribute router configuration commands, with their sequence numbers, can be entered in any order, making it easier to modify a router configuration. You can add new permit and deny access lists at the end of the configuration file instead of having to reenter all access lists in the desired order.
Figure 11-12 : Modified Configuration Example for Redistribution Using Route Maps Poor or Lost Connectivity in Multiprotocol Network Running Enhanced IGRP
Symptom: Nodes on a multi-protocol internetwork running IP Enhanced Interior Gateway Routing Protocol (Enhanced IGRP) and any combination of IGRP, RIP, OSPF, or other typically used routing protocols experience poor connectivity or lost connectivity with other nodes on the network. Table 11-20 describes possible causes and suggested actions when connectivity problems occur between nodes in a multiprotocol and IP Enhanced IGRP environment.
Poor or Lost Connectivity on Internetwork Running Enhanced IGRP Exclusively
Symptom: Nodes on an internetwork running IP Enhanced IGRP exclusively experience poor connectivity or lost connectivity with other nodes on the network. Table 11-21 describes possible causes and suggested actions for connectivity problems in an IP Enhanced IGRP-exclusive environment.
Table 11-21 : TCP/IP: Poor or Lost Connectivity on IP Enhanced IGRP-Exclusive Network
Enhanced IGRP Router Stuck in Active Mode
Symptom: An IP Enhanced IGRP router is stuck in Active mode. An Enhanced IGRP router can be in either Passive or Active mode. A router is Passive for Network A when it has an established path to Network A in its routing table.
If the Enhanced IGRP router loses the connection to Network A, it becomes Active for that network. The router sends out queries to all of its neighbors in order to find a new route to Network A. The router remains in Active mode until it has either received replies from all of its neighbors or until the active timer, which determines the maximum period of time a router will stay Active, has expired.
If the router receives a reply from each of its neighbors, it computes the new next hop to Network A and becomes Passive for that network. However, if the active timer expires, the router removes from its neighbor table any neighbors that did not reply, again enters Active mode, and issues a "Stuck-in-Active" message to the console:
Table 11-22 describes possible causes and suggested actions when an IP Enhanced IGRP router is stuck in Active mode.
Table 11-22 : TCP/IP: Enhanced IGRP Router Stuck in Active Mode
Copyright 1988-1996 © Cisco Systems Inc.
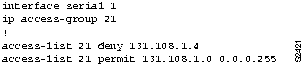
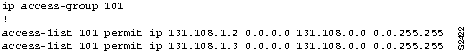
Possible Causes
Suggested Actions
No default gateway specification
Misconfigured subnet mask
Host interface is down
Router between hosts is down
Possible Causes
Suggested Actions
No default gateway
Misconfigured access list (getting routing information for some routes, but not others)
Discontinuous network addressing due to network design
Discontinuous network addressing due to link failure
Possible Causes
Suggested Actions
Misconfigured subnet mask
Misconfigured access list (host is denied by some router in the path)
Missing default gateway specification on remote host
Possible Cause
Suggested Actions
Misconfigured extended access list
Possible Causes
Suggested Actions
Discontinuous network due to failure. If Serial-Z is lost, traffic cannot traverse from Net-C1 to Net-C2 through RouterB1
Routing has not converged
Misconfigured access lists or other routing filters
Errors on serial link
Errors on Ethernet link
Possible Cause
Suggested Actions
Bridge or repeater in parallel with a router, causing updates and traffic to be seen as coming from both sides of an interface
Possible Cause
Suggested Actions
Misconfigured access list
Possible Causes
Suggested Actions
Subnet mask configuration mismatch between router and host
Misconfigured access list
No default gateway specified
Incorrect network specified
Routing Info
Host Value
Router Value
Destination IP address
192.31.7.49
192.31.7.49
Subnet mask
255.255.255.240
255.255.255.224
Interpreted address
Subnet address 48, host 1
Subnet address 32, host 17
Possible Cause
Suggested Actions
Improper OSPF mask specification
network 131.108.0.0 0.0.255.255 area 0
network 120.110.7.2 0.0.255.255 area 0
Possible Causes
Suggested Actions
Network is down
Misconfigured access list
Possible Cause
Suggested Actions
Missing network router configuration command
Possible Causes
Suggested Actions
A specific area is isolated from the OSPF backbone
Hello timer or dead timer intervals are mismatched in the OSPF domain
A virtual link is configured through a stub area
area area-id stub
area area-id virtual-link router-id
IGRP or RIP is not redistributed correctly into OSPF
A virtual link is misconfigured
area 1 virtual-link 108.31.1.1
area 1 virtual-link 121.10.1.1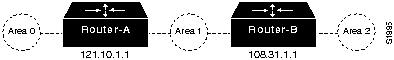
Possible Causes
Suggested Actions
Hello timer or dead timer intervals are mismatched in the OSPF domain
A virtual link is configured through a stub area
Possible Cause
Suggested Actions
Not all routers in stub area are configured as stubs
Possible Causes
Suggested Actions
Network is down
Misconfigured access list
Possible Cause
Suggested Actions
Missing default-metric command
Problem with the default administrative distance
Missing redistribute command
Misconfigured access list
Misconfigured distribute-list command
Possible Cause
Suggested Actions
Missing network router configuration command
router igrp 109
network 128.10.0.0
network 192.31.7.0
Possible Causes
Suggested Actions
Sequence numbers cause some conditions to be tested before others
Missing condition in the series of router redistribution commands
Possible Causes
Suggested Actions
IGRP, RIP, OSPF or other routing protocols are not enabled on boundary routers.
Router(config)# router igrp 100
Router(config-router)# network 193.166.66.0
Router(config-router)# network 193.168.25.0
Enhanced IGRP routing is not enabled on boundary routers.
Routes are not being redistributed between routing protocols.
Default routing metrics are incorrectly configured.
Possible Causes
Suggested Actions
Neighboring Enhanced IGRP routers are not visible to other Enhanced IGRP routers.
Routes are not being redistributed between two Enhanced IGRP autonomous systems.
Hello interval or hold time value mismatch
%DUAL-3-SIA: Route 198.169.52.51 Stuck-in-Active
The occasional appearance of these messages is not cause for concern. This is simply the manner in which an Enhanced IGRP router recovers if it does not receive replies to its queries from all of its neighbors. However, if these error messages occur frequently, the problem should be investigated.
Possible Causes
Suggested Actions
Active timer value is misconfigured
Interface or other hardware problem
Flapping route
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()