A common problem for any newly installed system is its inability to initialize itself correctly. This chapter addresses the following common router startup problems:
This discussion does not provide a step-by-step procedure. It is included as a checklist and should be used as a starting point for troubleshooting. The following discussion suggests a three-stage process:
Each of these stages is discussed separately.
When you are initially evaluating a router that is having a problem, keep the following three rules in mind:
At this stage, concentrate on problems that are obvious. Follow these inspection steps.
Note Platform-specific comments are noted in parenthetical additions to specific steps. Unless otherwise specified, all references to platform numbers (such as Cisco 7000) refer to the product series to which the platform belongs.
Step 1 Skip this step if you are troubleshooting an access router (Cisco 2000 series, Cisco 2500 series, Cisco 3000 series, Cisco 4000 series or IGS). For modular systems (except the Cisco 4000 and Cisco 7000), switch the power off and inspect the system for loose cards, cables, and port adapters. Reseat any that are loose. When cards are new, a thin film of carbon or oxidation buildup can prevent good contact. After reseating each card once or twice, you should achieve good contact.
- For the Cisco 4000 series systems, look for a loose network interface module (NIM). For the Cisco 7000 series systems, look for a loose Route Processor (RP), Switch Processor (SP), Silicon Switch Processor (SSP), or interface processor. Reseat any that are unseated. Be sure to use the ejector levers properly and to tighten all captive installation screws on the RPs, SPs, SSPs, interface processors, and power supplies. After reseating each card and tightening the captive installation screws, you should achieve good contact. For more information, refer to your hardware installation manual.
Step 2 Remove the chassis access panel and inspect the interior. Are the wires to the power supply connected correctly? Are wires burned or otherwise damaged?
Step 3 For systems other than Cisco 7000 series systems, look for damaged cards, backplanes, and ribbon cables. Are there any visibly crimped or shorted wires or cables?
Step 4 Check for missing or loose parts, incorrectly connected cables, and anything that appears out of place. Does the unit need to be cleaned? Is there damage to the interior or exterior?
Note Do not change anything before powering up the system for evaluation so that you can determine the source of suspected hardware problems during subsequent evaluation. Making changes can mask problems.
Applying Power and Evaluating the System
After you inspect the system, apply power to the unit and observe its behavior. If you suspect a hardware problem, follow these steps to evaluate operational conditions upon power-up:
Step 1 Power up the system (with system disconnected from a network).
- (When you power up a Cisco 7000 series system, the enabled LED on an SP, SSP, or interface processor will eventually go on if the card is seated correctly. If any enabled LEDs do not go on, power down the system and be sure that the cards are properly seated as discussed in the previous section, "Inspecting Your Router.")
Step 2 Compare system behavior against symptoms outlined in Table 2-1.
Step 3 If a failure does not fit the examples in Table 2-1, verify that the software in the processor and the microcode in the various cards are compatible with the individual card revisions within the chassis. Refer to the release document provided with your system.
Step 4 If the system boots, use the show controllers {token | mci | fddi | cbus} EXEC command to ensure that the interface hardware addresses are nonzero. Hardware addresses of all zeros will cause problems in a network.
- (For Cisco 7000 series systems, use the show controllers cxbus EXEC command and check the output of the show configuration privileged EXEC command. With downloadable microcode and software images stored in Flash memory, the system might be configured to load incompatible software or microcode.)
Note If the system boot-up sequence requires a password, the memory card and circuitry are working correctly. If the configuration in memory does not match the hardware configuration, problems can occur. Possible problems include hung ports, uninitialized ports, ping failures, bus timeout errors, and reboots.
Step 5 As a last resort, for systems other than Cisco 7000 series systems, you can use a voltmeter to ensure that all the power supply direct current (DC) voltages are within specifications. Refer to the configuration note (if one has been provided) for your power supply model.
 Warning Normally, you should turn off power to the chassis and unplug the power cord before accessing the chassis interior. However, if you are measuring power supply voltages, you must have power applied to the system. Use extreme caution when power is applied, and the internal chassis is exposed. Potentially harmful voltages are present. Only qualified router service technicians should perform power supply tests.
Warning Normally, you should turn off power to the chassis and unplug the power cord before accessing the chassis interior. However, if you are measuring power supply voltages, you must have power applied to the system. Use extreme caution when power is applied, and the internal chassis is exposed. Potentially harmful voltages are present. Only qualified router service technicians should perform power supply tests.
- For Cisco 7000 series systems, LEDs on the power supplies indicate whether power is within specification: the green alternating current (AC) power LED should be on and the red DC fail LED should be off. You can also use the show environment EXEC command to obtain a reading of the power supply voltages.
Note Configuration notes are only shipped with spares and replacement parts.
Table 2-1 : Router Power-Up Problems
| System appears to be dead
|
Power supply not seated properly (Cisco 7000); check LEDs on power supply
Fuse blown (Cisco 2000, Cisco 3000, Cisco 4000, and I, M, and C chassis)
Bad or tripped circuit breaker (A-type chassis)
Bad power supply
Bad switch
Bad backplane
Bad power cable or connector (to source or power supply port)
Bad or no input power (AC or DC)
|
| No fan or blower movement (MGS, CGS, Cisco 7000 series)
|
Bad fan
Bad blower
Bad 12V power supply (MGS, CGS)
Bad +24V power (Cisco 7000 series)
Shorted or broken wires on harness or backplane
|
| No blower movement (A-type, AGS+)
|
Bad blower
Bad circuit breaker
Tripped circuit breaker
Shorted or broken wires
Bad 110 or 220 VAC capacitor
|
| No power supply LEDs on or power supply Failed LED is on (Cisco 7000 only)
|
Power supply not seated properly
Bad input (source) power
Shorted or broken wires on harness or backplane
Environmental shutdown
|
| No LEDs on at boot for any card (except Cisco 7000)
|
Bad 5V power supply (no LEDs for problem card are on); box might boot
Shorted or broken wires
Bad backplane
Incompatible microcode on card with LEDs that do not go on
|
| No processor LEDs go on at boot; power supply LEDs are OK (Cisco 7000 only)
|
Partially inserted card has hung bus
Bad processor card or processor is poorly seated
Bad software or incompatible microcode
Shorted or broken wires on harness or backplane
Bad boot instructions in configuration file or corrupted image file in Flash memory
|
| Router will not boot
|
Bad power supply
Miswired power supply (except Cisco 7000 series)
Bad/disconnected console cable (system still boots; no monitor output)
Bad processor card or card is poorly seated
Bad software
Corrupted or incorrectly seated read-only memory (ROM)
Bent ROM pins
ROMs installed out of sequence
Bad nonvolatile random-access memory (NVRAM) card (except Cisco 7000 series)
Shorted wires (except Cisco 7000 series)
|
| System will not boot; boot error or CPU halt LED is on (Cisco 7000 series only)
|
Partially inserted card has hung bus
Bad processor card or processor is poorly seated
Bad software
Corrupted or incorrectly seated ROMs
Entire system image did not copy into Flash memory; Flash memory is full
|
| No cards show up in power-on message display
|
Bad backplane
Bad controller or interface card
Cards not seated in backplane
Conflicting or incompatible microcode version on card (or in Flash memory for Cisco 7000 series)
Bad power supply (except Cisco 7000 series)
|
| Cards missing from power-on message display
|
Bad controller or interface card
Cards not seated in backplane
Conflicting DIP switch setting on card with other devices (except Cisco 7000 series)
Card not supported with software version
Bad power supply (except Cisco 7000 series)
Bad arbiter (Cisco 7000 series)
|
| Circuit breaker trips or fuse blows (except Cisco 7000 series)
|
Bad power supply
Bad backplane
Shorted wires
Load too large on power supply
No load on power supply
Bad breaker
Bad blower
Bad card
|
| Constant or partial reboot
|
Bad processor, controller, or interface card
Poorly seated processor (Cisco 7000 series)
Bad backplane
Bad power supply (except Cisco 7000 series)
Bad software
Bad microcode
Poorly seated SIMMs (IGS, Cisco 2000, Cisco 2500, Cisco 3000, Cisco 4000, and Cisco 7000 series)
Poorly seated ROMs (CSC/3, CSC/4, RP, IGS)
|
Testing and Verifying Replacements
If you are replacing a part or card to remedy a suspected problem, remember the following rules:
- Make only one change at a time.
- Eliminate suspected problems one at a time.
- Think in terms of card replacement only.
- Keep track of any unrecorded failure symptoms or unexpected behaviors for future revisions of this guide.
- To test a system, start with a simple hardware configuration and add one card at a time until a failed interface appears or is isolated. Use a simple software configuration and test connectivity using a ping test.
Use Table 2-2 as the next step in evaluating hardware. The problems listed are not all of the possible failures for each product, but do represent commonly encountered symptoms. Where applicable, possible error messages associated with failure symptoms are also listed.
If you determine that a part or card replacement is required, contact your sales or technical support representative. Specific instructions concerning part or card installation are included with the configuration note provided with the replacement.
 Warning Before accessing the chassis interior and removing any cards, turn off power to the chassis. Use extreme caution around the chassis. Potentially harmful voltages are present. To prevent damage to components that are sensitive to electrostatic discharge (ESD), attach ESD protection before opening a chassis. Make certain that the power cord is connected, but that power is off. ESD damage prevention guidelines are provided in the hardware installation and maintenance publication for your router.
Warning Before accessing the chassis interior and removing any cards, turn off power to the chassis. Use extreme caution around the chassis. Potentially harmful voltages are present. To prevent damage to components that are sensitive to electrostatic discharge (ESD), attach ESD protection before opening a chassis. Make certain that the power cord is connected, but that power is off. ESD damage prevention guidelines are provided in the hardware installation and maintenance publication for your router.
If a part replacement appears to solve a problem, make certain to reinstall the suspect part to verify the failure. Always double-check a repair.
Note Any interface processor, the RP, the SP, or the SSP can prevent a Cisco 7000 series router from booting if the processor is not completely connected to the bus. Be sure to check the seating of processors if the system is not booting properly. Use the ejector levers to reseat all processor modules, then reboot.
Table 2-2 : Specific Cards and Products: Failure Symptoms and Associated Problems
| RP (Cisco 7000 series only)
|
System is down after running a short time; blower on.
System will not power up; blower on.
Boot Error or CPU halt LEDs might be on.
Configuration cannot be written to memory.
System will not boot (any combination of processor LEDs on, other than green LED alone).
The SP or SSP card is not recognized.
Partial boot only or system will not boot.
Random reboot occurs after initial boot.
System reboots when configuration memory is written.
No response from keyboard or apparent problem with console terminal.
Configuration memory is wrong size.
Error Indicators---Bad checksum for configuration memory, configuration memory not set up, nonvolatile memory not present.
|
| CSC-ENVM
|
System is down after running a short time; DC voltages off; blower on.
System will not power up; DC voltages off; blower on.
Configuration cannot be written to memory; system loses memory over time.
CSC-ENVM fails to shut system down even with excessive heat or DC voltage.
Error Indicators---Bad checksum for configuration memory, configuration memory not set up, nonvolatile memory not present.
|
| CSC/2, CSC/3, and CSC/4 cards
|
System will not boot (any combination of processor LEDs on, other than green LED alone).
Multibus cards are not recognized.
The ciscoBus controller is not recognized (CSC/3 and CSC/4 cards only).
Partial boot only.
Random reboot occurs after initial boot.
System will autoboot but cannot boot manually.
System will reboot when configuration memory is written.
No response from keyboard.
Error Indicators---Parity error, software versus hardware error, local timeout, bus error, wrong interface, emulation line error, software-forced crashes, checksum mismatch error.
|
| SP or SSP (Cisco 7000 series only)
|
Some or all CxBus cards are not recognized.
Enabled LED does not go on (processor card not initialized).
Error Indicators---MEMD failure, MEMA failure, arbiter/processor card failure.
|
| CSC-CCTL and CSC-CCTL2
|
Some or all ciscoBus cards are not recognized.
No LEDs are on.
All LEDs are on.
Some or all Multibus cards are not recognized.
Error Indicators---MEMD failure, MEMA failure, ciscoBus daughter controller failure.
|
| FIP (Cisco 7000 series only)
|
Not recognized by arbiter, SP, or SSP.
Fiber Distributed Data Interface (FDDI) ring will not come up.
FDDI ring comes up, but ping does not work on the FDDI ring or only works intermittently; only certain packet sizes ping.
No keyboard response after FDDI ring comes up; keyboard locks up.
Cannot see FDDI upstream/downstream neighbors.
LEDs are on in the wrong sequence.
FDDI ring comes up in "wrap-mode" only---wrap A or wrap B.
No ping through FDDI ring or to address of unit under test (UUT); intermittent ping.
FDDI ring will intermittently or constantly transition.
Ring status LEDs do not go on.
Error Indicators---Unknown data error, card in slot n does not respond.
|
CSC-FCI, CSC-C2FCI, and CSC-C2FCIT cards
|
Not recognized by ciscoBus controller.
FDDI ring will not come up.
FDDI ring comes up, but ping does not work on the FDDI ring or only works intermittently; only certain packet sizes ping.
No keyboard response after FDDI ring comes up; keyboard locks up.
Cannot see FDDI upstream/downstream neighbors.
Error Indicators---Unknown data error, MEMD failure, MEMA failure, ciscoBus daughter controller failure.
|
FDDI appliques (APP-LMM, APP-LMS, APP-LSM, and APP-LSS)
|
FDDI ring will not come up.
LEDs are on in wrong sequence.
FDDI ring comes up in "wrap-mode" only---wrap A or wrap B.
No ping through FDDI ring or to address of UUT; intermittent ping.
FDDI ring intermittently or constantly transitions.
Cannot see FDDI upstream/downstream neighbors.
Ring status LEDs are not on.
|
| EIP (Cisco 7000 series only)
|
Card is not recognized by the arbiter, SP, or SSP.
Unable to ping on any or some ports; intermittent ping; only certain packet sizes will ping.
All LEDs are on.
No LEDs are on.
Wrong number of LEDs are on.
Error Indicators---Timeout, arbiter, SP, or SSP failure, halted output.
|
| CSC-MEC and CSC-C2MEC cards
|
Card is not recognized by ciscoBus controller.
Unable to ping on any or some ports; intermittent ping; only certain packet sizes will ping.
All LEDs are on.
No LEDs are on.
Wrong number of LEDs are on.
Error Indicators---Multibus timeout, ciscoBus daughter controller failure, halted output.
|
| FSIP card (Cisco 7000 series only)
|
Card is not recognized by arbiter or SP or SSP.
No LEDs are on.
All LEDs are on.
No ping on any or some ports; DTE will ping and DCE will not ping (or vice versa); intermittent ping; only certain packet sizes will ping.
Ports will not initialize---some or all.
Will not netboot or ping to network; no ping to address of unit under test (UUT).
Error Indicators---Local timeout, MEMD failure, MEMA failure, halted output, bus or ALU failure, configuration memory not set up, excessive input serial errors, CxBus timeouts, or SxBus timeouts (SxBus timeouts apply to older Cisco 7000 routers only).
|
| FSIP port adapters
|
Interface up, but ping does not work, or intermittent ping functionality.
DTE will ping but DCE will not ping (or vice versa).
System reboots.
|
CSC-MCI and CSC-SCI
|
Card is not recognized by the processor card.
No LEDs are on.
All LEDs are on.
No ping on any or some ports; DTE will ping but DCE will not ping (or vice versa); intermittent ping; only certain packet sizes will ping.
Ports will not initialize---some or all.
Will not netboot or ping to network; no ping to address of UUT.
CSC-MCI-3 card cannot see random-access memory (RAM) and NVRAM.
Wrong number of LEDs on---too many or too few.
Error Indicators---Local timeout, MEMD failure, MEMA failure, halted output, bus/ALU failure, configuration memory not set up, excessive input serial error, or Multibus timeouts.
|
| Arbiter, SP, or SSP (Cisco 7000 series only)
|
Cannot write configuration memory on RP; no memory access; memory access causes reboot.
CxBus cards are not recognized.
System will not boot or will reboot.
No DC voltages---some or all.
Bad power supply (caused by shorted backplane).
Blower is not working.
Systems consistently crash when attempting to boot.
|
ciscoBus backplane and Multibus backplane
|
Cannot write configuration to memory; cannot access memory; memory access causes reboot.
Multibus or ciscoBus cards are not recognized.
System will not boot or will reboot.
No DC voltages---some or all.
Bad power supply (caused by shorted backplane).
|
| TRIP card (Cisco 7000 series only)
|
Card is not recognized by the processor.
No ping to outside address or address of UUT; intermittent ping.
No hardware address recognized.
Error Indicators---Halted output, beaconing, local timeout, Open failed: lobe test.
|
CSC-R, CSC-R16M, CSC-1R, CSC-2R, and CSC-C2CTR cards
|
Card is not recognized by the processor.
No ping to outside address or address of UUT; intermittent ping.
No hardware address recognized.
Error Indicators---Halted output, beaconing, local timeout, Open failed: lobe test, Multibus timeout.
|
CSC-M, CSC-MT, CSC-MC, and CSCMC+ cards
|
NVRAM not recognized by MCI-3, CSC-1R, or CSC-2R card (CSC-MC and CSC-MC+ cards only).
Configuration cannot be written to memory.
Memory lost over time.
Configuration and/or Multibus memory wrong size (CSC-MT card only).
Error Indicators---Bad checksum for configuration memory, configuration memory not set up, nonvolatile memory not present.
|
Serial appliques
|
Interface up but ping does not work, or intermittent ping functionality.
DTE will ping, DCE will not ping (or vice versa).
System reboots (with dual-mode V.35, suggests bad ground contact).
5V or 12V power supply LEDs indicate no power detected.
|
| Cisco 4000
|
System will not boot.
Fuse blows.
Constant or partial reboot.
|
IGS, Cisco 2000, Cisco 2500, and Cisco 3000
|
System will not boot.
Fuse blows (except Cisco 2500 series).
Fan does not run.
Constant or partial reboot.
|
| 500-CS
|
System will not boot.
Fuse blows.
Fan does not run.
LEDs fail to go on.
|
Troubleshooting Media Problems
Table 2-3 through Table 2-6 summarize general problem-solving guidelines for common media (Ethernet, Token Ring, serial lines, and FDDI).
Table 2-3 : Media Problems: Ethernet
| Excessive errors or noise on Ethernet
|
Step 1 Use the show interfaces ethernet EXEC command to determine the status of the interface.
Step 2 Use a time domain reflectometer (TDR) to find any unterminated Ethernet cables.
Step 3 Check host cables to determine whether any are incorrectly terminated, overly long, or damaged.
Step 4 Look for a jabbering transceiver attached to a host (might require host-by-host inspection).
Step 5 Look for badly spaced taps causing reflections.
|
Table 2-4 : Media Problems: Token Ring
| Nonfunctional Token Ring
|
Step 1 Use the show interfaces token command to determine the status of the interface.
Step 2 If the status line indicates that the interface and line protocol are not up, check the cable from router to Multistation Access Unit (MAU). Make sure that the cable is good; replace if necessary.
- If you are performing a new installation, make sure that the MAU has been properly initialized. Consult the manufacturer's documentation for information on initializing your MAU.
Step 3 If the show interfaces token output indicates that the interface and line protocol are up, use the ping command between routers to test connectivity.
Step 4 If the remote router does not respond, check the ring specification on all nodes attached to the Token Ring backbone. Ring speed for all must be the same. The options are 4 Mbps (default) and 16 Mbps. Use the write terminal privileged EXEC command to determine which speed is active.
Step 5 If necessary, modify ring speed specifications for clients, servers, and routers.
Step 6 Use the ring-speed interface configuration command to modify the ring speed configuration for Token Ring cards that support software speed configuration; change jumpers as needed for modular router platforms that do not support software speed configuration. For more information about ring speed specifications, refer to the hardware installation and maintenance manual for your system.
|
Table 2-5 : Media Problems: Serial Lines
| Nonfunctional serial line
|
Step 1 Use the show interfaces serial EXEC command to determine the status of the interface.
Step 2 If the show interfaces serial command indicates that the interface and line protocol are up, use the ping EXEC command between routers to test connectivity. Isolate possible circuit problems by looping the local DTE back to the RTS interface pin.
Step 3 If routers do not respond to the ping test, follow the troubleshooting techniques as discussed in the "Troubleshooting Serial Line Problems" chapter.
Step 4 If clock and data signals are out of phase, invert the clock signal.
|
Table 2-6 : Media Problems: FDDI
| Nonfunctional FDDI ring
|
Step 1 Use the show interfaces fddi EXEC command to determine status of interface.
Step 2 If the show interfaces fddi command indicates that the interface and line protocol are up, use the ping command between routers to test connectivity.
Step 3 If the interface and line protocol are up, make sure the media access control (MAC) addresses of upstream and downstream neighbors are as expected.
- If all zeros appear in either of the address fields for these neighbors, a physical connection problem is likely.
Step 4 In this case (or if status line does not indicate that the interface and line protocol are up), check patch-panel connections or use an optical TDR or light meter to check connectivity between neighbors. Ensure that signal strength is within specification.
|
Upstream neighbor has failed and bypass switch is installed.
Bypass switches can cause signal degradation because they do not repeat signals like a normal transceiver.
|
Step 1 Check upstream neighbor to determine if it is operational.
Step 2 If the node is down, and a bypass switch is in place, resolve any problems found in upstream neighbor.
|
Troubleshooting Router Booting Problems
Routers allow for system initialization (booting) using several methods. Systems can be booted in any of four ways:
- From a file over the network
- From Flash memory
- From ROM
- From a PCMCIA Flash memory card
The material that follows addresses problems that might arise during the booting process.
Booting Troubleshooting Information
If you are unable to resolve your booting problem, collect the following information for the technical support representative:
- ROM images (using the show version EXEC command)
- Programmable ROM labels
- NVRAM configurations for client and adjacent routers (via the write terminal privileged EXEC command)
- Debugging output from the adjacent router using the following privileged EXEC commands:
- debug ip packet
- debug arp
- debug ip udp
- debug tftp
- For more information about these debug commands, refer to the Debug Command Reference publication.
Notes on Netbooting
Routers support netbooting via both the Trivial File Transfer Protocol (TFTP) and the DEC Maintenance Operation Protocol (MOP) across all supported media types such as Ethernet, FDDI, serial lines, Token Ring, and High-Speed Serial Interface (HSSI). During netbooting sessions, routers behave like hosts: they route via proxy Address Resolution Protocol (ARP), Serial Line Address Resolution Protocol (SLARP) information, Internet Control Message Protocol (ICMP) redirects, or a default gateway. When netbooting, routers ignore dynamic routing information, static IP routes, and bridging information. As a result, intermediate routers are responsible for handling ARP and User Datagram Protocol (UDP) requests correctly. For serial and HSSI media, ARP is not used.
If you need to netboot from a server, you should first ping the server from the ROM software. If you are unable to ping the server, first look for a solution in Table 2-7. If none of the problems described in Table 2-7 explains the ping failure, there is probably a problem with the server configuration or hardware. Contact your router or TFTP server technical support representative for assistance.
Using a Fault-Tolerant Boot Strategy
Network failures can make netbooting impossible. After Flash memory is installed and configured, configure the router to boot in the following order to reduce the effects of a server or network failure:
- Boot an image from Flash memory
- Boot an image from a system filename (netboot)
- Boot from a ROM image
Example
The order of the commands needed to implement this strategy is illustrated in the following sample output:
klamath# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
klamath(config)# boot system flash gsxx
klamath(config)# boot system gsxx 131.108.1.101
klamath(config)# boot system rom
klamath(config)# ^Z
klamath#
%SYS-5-CONFIG_I: Configured from console by console
klamath# write memory
[ok]
klamath#
Using this strategy, a router has three sources from which to boot: Flash memory, netboot, or ROM. Providing alternative sources can help to mitigate any potential failure of the TFTP server or the network.
Note The configuration register must be set to allow ROM image booting following failed netbooting attempts. Refer to the hardware configuration manual for your router product.
Timeouts and Out-of-Order Packets
When netbooting, it is not unusual for a client to retransmit requests before receiving a response to an initial ARP request. The retransmissions can result in timeouts, out-of-order packets, and multiple responses. Timeouts (shown as periods in a netbooting display) and out-of-order packets (shown as uppercase Os) do not necessarily prevent a successful boot. It is acceptable to have either or both of these in the first few packets. Exclamation points represent good packets. The following examples show successful netbooting sessions even though timeouts and out-of-order packets have occurred:
Booting gs3-bfx from 131.108.1.123: !.!!!!!!!!!!!!!!!!!!!!!!
Booting gs3-bfx from 131.108.1.123: !O.O!!!!!!!!!!!!!!!!!!!!!!
If your session has many out-of-order packets and timeouts, the problem will require some attention. Problems that might result in timeouts and out-of-order packets and recommended solutions are discussed in the troubleshooting tables that follow.
Router Booting Process Symptoms
Booting problem symptoms are discussed in the following sections:
Router Cannot Netboot from TFTP Server
Symptom: In the most general case, a router tries to obtain its system image over the network, but fails. Netbooting failures can result from several problems. Following is an example display generated by the system when it cannot boot:
Booting gs3-bfx..........[failed]
Table 2-7 outlines possible causes and suggests actions for when a router cannot boot from a TFTP server. Other specific symptoms and problems are outlined in subsequent discussions.
Note Refer to the host (boot server) manual for details about setting up a TFTP server.
Table 2-7 : Router Startup: Router Cannot Netboot from a TFTP Server
| Network is disconnected or isolated
|
Step 1 Boot the router from ROM or Flash memory if possible.
Step 2 Use the ping EXEC command to send a message to the broadcast address (255.255.255.255).
Step 3 Look for an ICMP Echo Reply response for a TFTP server.
Step 4 If no response occurs, use the show arp EXEC command to look for an entry associated with the server.
Step 5 Use the show ip route EXEC command to look for an entry listing the network or subnet for the server.
- If a path to a boot server exists, a disconnected network is not the problem. If no path exists, make sure that a path is available before continuing to attempt router netbooting.
|
| TFTP server is down
|
Step 1 Check the intended server system to determine whether the TFTP server is running. You can do this by attempting to make a TFTP connection from the boot server to itself. The connection will be successful if the TFTP server is running.
Step 2 If the TFTP server is not running, initialize it. The actual initialization process varies depending on the type of boot server.
- (For a BSD UNIX server, check the /etc/inetd.conf file. If the TFTP server is not included in this file, add the appropriate line and cause inetd to reload its configuration.)
|
| Misconfigured server (router image in wrong directory)
|
Step 1 Look at the server configuration file to see if it points to the directory in which the router image resides.
Step 2 Move the router image to the correct directory if necessary.
Step 3 Make sure the /tftpboot directory is reachable over the network.
|
| Misconfigured server (router system image file permission is incorrect)
|
Step 1 Check the permission of the file.
Step 2 If necessary, change the permission. For example, for a UNIX boot server, set the permission for the file to owner read/write, group read, and global read (the UNIX command for setting this permission is chmod 0644).
|
| Misconfigured server (bad protocol address)
|
Step 1 Check the server configuration file for the IP address of the host.
Step 2 Change if incorrect.
|
| Server requires default gateway configuration
|
Step 1 Check the router configuration file for the ip default-gateway global configuration command, which defines a default gateway.
Step 2 Refer to the section "IP Default Gateway Configuration Notes" later in this chapter for more information about configuring default gateway support.
|
| Misconfigured router (bad server address specification in boot system global configuration command)
|
Step 1 Check the router configuration file for the boot server address (IP address of a TFTP server or MAC address of a MOP server).
Step 2 Change if necessary.
|
| Misconfigured router (bad router address specification)
|
Step 1 Check the router configuration file for the router address (IP address only).
Step 2 Change if not correct.
|
| Misconfigured router (wrong filename)
|
Step 1 Check the router configuration file for boot filename.
Step 2 Change as necessary. (Check the host's documentation for details about setting the name of the system image on the TFTP server.)
- Note that some versions of the ROM are case sensitive. Contact your router technical support representative for specific details.
|
Misconfigured router (wrong configuration register setting)
|
Step 1 Check the configuration register setting for your system.
- (If you want to boot from a server over the network, you must set the configuration register appropriately. The specific configuration for netbooting depends on the platform that is being booted.)
Step 2 Determine whether you want to manually or automatically netboot from a TFTP server. To manually netboot, the configuration register must set to 0x0; otherwise, you will be netbooting automatically using the default system image name or one specified with the boot system global configuration command.
- Refer to your configuration, command reference, and hardware installation and maintenance publications for more details about setting the configuration register.
|
Incorrect filename
|
Step 1 Compare the router image filename on the boot server with the name specified in the router configuration.
Step 2 Make sure they match.
|
Timeouts and Out-of-Order Packets Occur during Netbooting
Symptom: Timeouts (shown as periods on a netbooting display) and out-of-order packets (shown as uppercase Os) might prevent systems from netbooting. Depending on the cause, the number of timeouts and out-of-order packets indicated on the router's console display can vary---suggesting different underlying problems.
The following example shows a netbooting session that contains excessive timeouts and out-of-order packets:
Booting gs3-bfx from 131.108.1.123: !O.O!.O..O!!!OOO.O!!.O.O.....
It is possible that the client router will boot under this situation. However, when excessive timeouts and out-of-order packets are occurring, there is probably some kind of problem on the network, and netbooting (as well as network service availability) may be inconsistent.
Table 2-8 outlines possible causes and suggests actions to take when timeouts or out-of-order packets prevent a netboot.
Table 2-8 : Router Startup: Timeouts and Out-of-Order Packets Prevent Booting
| Link is saturated
|
Step 1 Boot the router from ROM and ping the server. Determine whether timeouts and out-of-order packets appear.
Step 2 Check local network concentrators for excessive collisions on the same network.
- (If excessive collisions are encountered, try reorganizing your network topology to reduce collisions.)
Step 3 Use an appropriate show interfaces EXEC command on routers in the path or place a network analyzer between the router and server.
Step 4 Look for dropped packets and output errors.
Step 5 If approximately 15 percent or more of the traffic is being dropped or any output errors occur, congestion might be the problem.
Step 6 Wait until the traffic subsides before attempting to netboot the router. If the problem is chronic, increase bandwidth or move the server closer to the router being booted.
|
| Link is broken, possible routing loops
|
Step 1 Check the continuity of the path from the booting router to the boot server using ping or trace EXEC commands.
Step 2 If a break is found, restore link between router and boot server.
|
Netbooting Problems Resulting from Invalid Routing Paths
Symptoms: As a TFTP client, the router can determine the path to a TFTP server using ARP. Using this technique, the router sends TFTP packets over the same path from which it received an ARP response. If this path becomes invalid, packets sent from the router to the server might fail even though the router has successfully received an ARP response to its ARP request. If the router is sending packets over an invalid path, a message similar to one of the following is displayed on the console:
Booting gs3-bfx!OOOO..........[timed out]
Booting gs3-bfx!.O.O.O.O..........[timed out]
Booting gs3-bfx!!!!!!!!!!OOOOOOOOOO..........[timed out]
In some cases, you also might notice that there is an initial response from a server, but that the netboot sequence still fails. The boot message would be similar to the following:
Booting gs3-bfx!..........[failed]
Note A limitation of proxy ARP is that a device can answer at any time, even after the router has received a response and identified a path to the server. The ARP implementation of the router uses the path designated by the most recent ARP response when routing traffic using ARP information.
Table 2-9 outlines possible causes and suggests actions when invalid routing paths prevent netbooting.
Table 2-9 : Router Startup: Invalid Routing Paths Prevent Netbooting
| Bad routing paths on neighbor routers
|
Step 1 Verify that neighbor routers can ping the server.
Step 2 Use the trace EXEC command to determine their paths to the server.
Step 3 Use the show arp or show ip route EXEC command to examine the ARP tables or IP routing tables of the neighbor routers to verify that the server is listed and that the routing table entries are appropriate.
Step 4 Use the clear arp-cache and clear ip-route privileged EXEC commands as necessary.
Step 5 Attempt to netboot the router again.
|
| Problems caused by multiple paths
|
Step 1 Shut down all extra interfaces except the one over which you intend to netboot the router.
Step 2 Use the no ip proxy-arp interface configuration command on all neighboring routers to shut down their ability to provide proxy ARP responses.
- Make this change with care because it can cause problems for other network traffic.
- As an alternative, boot the router from ROM and configure the ip default-gateway global configuration command if you do not want to disable proxy ARP. Use of this command is discussed briefly in the following section "IP Default Gateway Configuration Notes."
Step 3 Try to netboot the router.
|
IP Default Gateway Configuration Notes
To send IP packets to other stations on the same network, an end station must have an IP address and a network mask. A router discovery protocol, such as the ICMP Router Discovery Protocol (IRDP) or the Gateway Discovery Protocol (GDP), can be used to learn new addresses. Another way to facilitate communication is to use proxy ARP, which, when supplied by a router, allows an end station to believe that other stations are on the same network, even though the other stations are actually behind the router that is supplying proxy ARP.
Some system images do not support IRDP, GDP, and proxy ARP. The system images that do not support IRDP, GDP, and proxy ARP are the igsrxboot image, which is the system image stored in the Cisco 3000 EPROM, and the xx-rxboot image, which is the system image stored in the Cisco 4000 EPROM. These system images do not contain the IP routing software found in the EPROMs of other router models. Instead, they are smaller images that are capable of booting from Flash memory and of netbooting. When Flash memory does not contain a valid image, use the copy tftp flash privileged EXEC command to copy a fully functional system image from a TFTP server to Flash memory.
If you have booted a local router using the igs-rxboot image or the xx-rxboot image, and you need to obtain a system image from a TFTP server that is on a different network and the intervening router does not support IRDP, GDP, or proxy ARP for the port adjacent to the local router, the local router must have the ip default-gateway global configuration command in its configuration to identify the IP address of the intervening router.
Note During netbooting, IP routing information (including static routing information) is ignored, so the ip default-gateway global configuration command is also useful when netbooting a router that does include IP routing software in its EPROM.
Consider a case in which the Flash memory of a Cisco 2500, a Cisco 3000, or a Cisco 4000 has no usable image due to an error, such as copying an incorrect image to it. If a reboot occurs, the only image available to run is the xxrxboot image. Use the copy tftp flash privileged EXEC command to copy a new system image to the Cisco 4000. Before you can use the copy tftp flash command, you must include the ip default-gateway global configuration command in the Cisco 4000's configuration to reach a remote TFTP server. A sample session illustrating the use these commands follows:
router(boot)# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
ip default-gateway 130.108.1.7
^Z
%SYS-5-CONFIG_I: Configured from console by console
router(boot)# copy tftp flash
IP address or name of remote host [255.255.255.255]? server1
Name of tftp filename to copy into flash []? IJ09140Z
copy IJ09140Z from 131.131.101.101 into flash memory? [confirm] <Return>
xxxxxxxx bytes available for writing without erasure.
erase flash before writing? [confirm] <Return>
Clearing and initializing flash memory (please wait)####...
Loading from 131.131.101.101: !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!... [OK - 324572/524212 bytes]
Verifying checksum...
VVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVVV...
Flash verification successful. Length = 1204637, checksum = 0x95D9
Client ARP Requests Time Out when Netbooting
Symptoms: When netbooting via a path that requires the client to use proxy ARP, the router being netbooted sends an ARP request to the server over every available network interface configured for IP. The router expects the server or an intermediate system to return an ARP response. If the router does not receive an ARP response, a message similar to the following is displayed at the console:
Booting gs3-bfx..........[timed out]
Table 2-10 outlines possible causes and suggests actions when client ARP requests time out during a netboot.
Table 2-10 : Router Startup: Client ARP Requests Time Out during Netboot
| Wrong filename or other configuration problem
|
Step 1 Check the filename definition and path specified on the server.
Step 2 Check the problems discussed earlier in this section under the symptom "Router Cannot Netboot from TFTP Server."
|
| Intermediate routers have ARP filtering enabled
|
Step 1 Boot the router from ROM.
Step 2 Make sure you can ping the server from the router.
Step 3 Try the write network privileged EXEC command to test TFTP connectivity with the server.
Step 4 If these steps are successful, at the intermediate router check the configuration using the show arp EXEC command.
Step 5 Enable the debug arp privileged EXEC command to determine whether neighbor proxy ARP responses are being generated.
Step 6 If the neighbor is not sending proxy ARP responses and its configuration contains the no ip proxy-arp interface configuration command, disable ARP filtering by removing the entry.
- Note that proxy ARP is enabled by default.
Step 7 If you need to have a no ip proxy-arp entry in the neighbor router configurations, use the ip default-gateway global configuration command in the router. Use of this command is discussed briefly in the section "IP Default Gateway Configuration Notes," earlier in this chapter.
|
| Configuration of the serial interface on the router being netbooted includes a broadcast destination, but an intermediate router does not have the required IP helper address defined to point to the TFTP server
|
Step 1 Check the configurations of all routers in the path.
Step 2 Include helper addresses as required using the ip helper-address interface configuration command.
- If you are unicasting to your server, you do not need to use the IP helper address, but if you are broadcasting to 255.255.255.255 (by omitting the IP address of the server), add the ip helper-address command on the neighboring router interface used in the netbooting broadcast.
|
Vector Errors Occur when IGS Attempts Netbooting
Symptom: For an IGS attempting netbooting, console display indicates "vector errors." Figure 2-1 illustrates an example of the kind of message that will appear.
Figure 2-1 : Example Vector Error Output

Table 2-11 outlines a possible cause and suggests actions when vector errors occur during a netboot.
Table 2-11 : Router Startup: Vector Errors Occur during Netbooting
| The IGS is attempting to boot a compressed system image (for Software Release 9.0 and earlier versions)
|
Step 1 On the boot server, check the software image file type.
- (For example, use the UNIX command file image-name at a UNIX-based server. If the file is compressed, the server will return a "compressed file" message.)
Step 2 Uncompress the file using the uncompress image-name command (in UNIX) or equivalent.
Step 3 Try to netboot the router.
|
Buffer Overflow Errors Occur when Netbooting
Symptom: When netbooting a router, the console display indicates that "buffer overflow" has occurred, and the router is unable to boot. Table 2-12 outlines possible causes and suggests actions when buffer overflows occur during the netboot process.
Table 2-12 : Router Startup: Buffer Overflow Errors Occur during Netboot
| Not enough memory to boot image (Cisco 2500 and Cisco 4000)
|
Step 1 Use the show version EXEC command to determine the amount of installed memory.
Step 2 Upgrade to 16 megabytes (MB) of memory.
|
| Not enough memory to boot image (IGS)
|
Step 1 Use the show version EXEC command to determine the amount of installed memory.
Step 2 Upgrade to 4 MB if necessary.
|
| Not enough memory in router to boot image (CSC/3 card running Software Release 9.1)
|
Step 1 For systems that have a CSC/3 card and 9.1 ROMs, you must netboot a compressed image. Compressed image files usually have names that end with a .Z extension (although this is not a requirement). Compressed images netboot exactly like uncompressed images; the router uncompresses the image after it is loaded.
Step 2 If the CSC/3 card is running Software Release 9.0 or 9.1, increase the memory efficiency of the decompression algorithm by upgrading to the maintenance release recommended by your technical support representative.
|
Undefined Load Module Error when Netbooting
Symptom: When netbooting a router, the console display indicates "undefined load module" error, and the router is unable to boot. Table 2-13 outlines a possible cause and suggests actions when an undefined load module error occurs during a netboot.
Table 2-13 : Router Startup: Undefined Load Module Errors Occur during Netboot
| Attempting to netboot router configuration (text) file
|
Step 1 If you are booting manually, refer to the Getting Started Guide for your router to see the proper command line format.
Step 2 Check the router configuration file.
Step 3 Compare the filename specified in the global configuration command boot system filename [address] entry with the actual router image filename. Make sure they match.
Step 4 If they differ, change the name in the configuration file.
|
Note Remember to use the router image filename in the boot system global configuration command specification and the configuration filename with the boot host and boot network global configuration commands.
Router Cannot Boot from Another Router (TFTP Server)
Symptom: When booting a router from another router acting as a TFTP server, the router is unable to initialize properly. This symptom can be caused by any of the problems outlined in the preceding netbooting symptom discussions.
This section focuses on the problems of routers that are acting as TFTP servers. Table 2-14 outlines possible causes and suggests actions when a router cannot boot from other routers.
Table 2-14 : Router Startup: Router Is Unable to Boot from Another Router
| Misconfigured TFTP server/router (missing or incorrect tftp-server global configuration command)
|
Step 1 Use the write terminal privileged EXEC command to determine whether the tftp-server system global configuration command is missing or incorrectly specified.
Step 2 Add or modify the tftp-server system global configuration command as necessary on the router intended to be the TFTP server. Specify the name of a file in Flash memory.
|
| Wrong/incomplete image in Flash memory
|
Step 1 Use the show flash EXEC command to determine whether the image is incomplete. This display might show that the image is
deleted and indicate the reason. Figure 2-2 shows an example of show flash output.
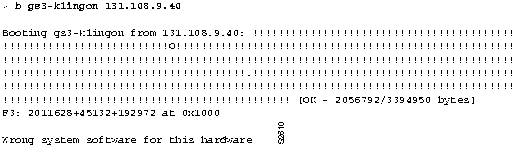
- Figure 2-3 illustrates the "wrong system software" message that is displayed when a router attempts to boot an incorrect image. In this case, the router is being booted from the ROM monitor.
Step 2 Obtain the correct image.
- (If necessary, contact your router technical support representative to determine which image is correct.)
Step 3 When you identify the correct image, use the privileged EXEC command copy tftp flash at the router to retrieve the image.
|
Figure 2-2 : show flash Command Output Indicating Image Is Deleted
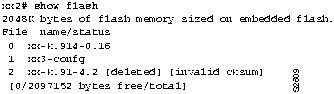
Figure 2-3 : ROM Monitor Output when Attempting to Boot an Incorrect Image
Local Timeouts Occur when Booting from ROM
Symptom: When a router is booting from ROM, the processor might be unable to access a portion of the system memory. If this is the case, the router will be unable to complete its boot process and will not start the ROM monitor. Table 2-15 outlines a possible cause and suggests actions when local timeouts occur when booting from ROM.
Table 2-15 : Router Startup: Local Timeouts Occur when Booting from ROM
Bad EPROM, bent pin, EPROM in wrong socket, or EPROM poorly seated
(Generally, this only occurs if you have just replaced your system EPROMs.)
|
Step 1 Power off system.
Step 2 Physically inspect each EPROM.
Step 3 Make sure each EPROM is correctly positioned in the socket (with notches properly aligned) in the correct socket.
Step 4 If a pin is bent, straighten it carefully. Reinstall the EPROM and power on the system. If a pin breaks off, the EPROM must be replaced.
Step 5 If an EPROM has been installed backward, and power has been applied to it, the EPROM has been damaged and must be replaced.
Step 6 If local timeouts persist, contact you router technical support representative.
|
Router Hangs after ROM Monitor Initializes
Symptom: When booting a Cisco 7000 series, AGS+, AGS, ASM-CS, MGS, IGS, or CGS router from ROM, the systems might hang after the ROM monitor initializes.
Table 2-16 outlines possible causes and suggests actions when a router hangs after the ROM monitor initializes.
Table 2-16 : Router Startup: Router Hangs after ROM Monitor Initializes
| Incorrect EPROM size setting
|
Step 1 Power off system.
Step 2 Inspect EPROM size jumper(s). Refer to the hardware installation and maintenance publication for your router to determine the proper setting.
Step 3 Modify as required.
|
| Configuration register is not set correctly
|
Step 1 Power off system.
Step 2 Check your configuration settings (boot ROM jumpers and software configuration). If no jumper is set at bit 0, and no other boot field is defined, you must reconfigure your system so that it can boot properly.
Step 3 To enable your router to boot properly, do one of the following:
- Configure the software configuration register of the router using the config-register value global configuration command. (This applies to the IGS, Cisco 2500, Cisco 3000, and Cisco 7000 platforms running Cisco Internetwork Operating System (Cisco IOS) Release 10.0 or later in the EPROM.)
- Set the boot ROM jumper to permit booting.
- Include the correct boot system global configuration commands to boot the system.
- Set bit 0 to a value of 1 to force booting from ROM.
- Refer to your configuration, reference, and hardware installation and maintenance publications for more information about configuring your router for the various booting options.
|
Router Is Stuck in ROM Monitor Mode
Symptom: When booting a router from ROM, the system boots into ROM monitor mode, but does not boot the complete system image. Table 2-17 outlines possible causes and suggests actions when a router is stuck in ROM monitor mode.
Table 2-17 : Router Startup: Router Is Stuck in ROM Monitor Mode
| Incorrect configuration register setting
|
Step 1 At ROM monitor prompt (
>
), enter b to boot the system.
Step 2 If a configuration exists in NVRAM, the system will display the vacant message. Press the Return key to continue.
- If a configuration does not exist in NVRAM, the setup menu appears. For the purposes of this activity, skip the setup process.
Step 3 Use the show version EXEC command to determine the configuration register setting.
Step 4 Look for an invalid configuration register setting. The default is 0x101, which disables the Break key and forces the router to boot from ROM. A typical "bad" setting has a zero in the least significant bit (for example 0x100).
- (For more details about setting the configuration register, refer to your hardware installation and maintenance publication.)
|
| Break key pressed during boot process (Software Release 9.1 and later)
|
Step 1 At the ROM monitor prompt, enter c to allow router to continue booting.
|
| Console cable inserted or removed during boot process, or console power-cycled during boot process (Software Release 9.1 or later)
|
Step 1 Press the Return key.
Step 2 Look for the ROM monitor prompt (
>
).
Step 3 If this prompt appears, enter c at the prompt to continue the booting process.
|
Scrambled Output when Booting from ROM
Symptom: When booting from ROM, the router displays indecipherable textual output on the monitor. Table 2-18 outlines possible causes and suggests actions when output is scrambled while booting from ROM.
Table 2-18 : Router Startup: Scrambled Output when Booting from ROM
| Wrong terminal speed setting or wrong configuration register setting
|
Step 1 Use the monitor setup menu to check the terminal line speed setting for the monitor.
Step 2 Check the terminal speed configured on the router as specified in the configuration register setting (default is 9600 baud, 8 databits, 2 stop bits, and no parity).
Step 3 If the terminal speed of the monitor and the router do not match, modify as necessary.
- (Refer to your hardware installation and maintenance documentation for details about setting up the monitor.)
|
Bad router hardware
An example is a bad dual universal asynchronous receiver transmitter (DUART). The DUART controls the system console and auxiliary ports. A failed DUART causes the far left LED on a CSC/3 or CSC/4 card to blink repeatedly.
|
Step 1 Troubleshoot router hardware as discussed in the section "Diagnosing Router Hardware Problems," earlier in this chapter.
|
Vector Error Occurs when Booting from Flash Memory
Symptom: When booting a router from Flash memory, the system display indicates that a vector error occurred. Table 2-19 outlines possible causes and suggests actions when vector errors occur when booting from Flash memory.
Table 2-19 : Router Startup: Vector Errors Occur when Booting from Flash Memory
| Compressed system image (Cisco 2000, Cisco 2500, Cisco 3000, and Cisco 4000)
|
Step 1 Power cycle the router.
Step 2 Within the first minute of booting, press the Break key to access the ROM monitor.
Step 3 At the ROM monitor prompt (
>
), enter o/r (without arguments) to set the configuration register to boot from ROM.
Step 4 Enter b to boot (router enters setup mode).
Step 5 Press Ctrl-C to bypass setup.
Step 6 Enter the configure memory privileged EXEC command.
Step 7 Obtain an uncompressed system image. You can do this as follows:
- From the router prompt, use the privileged EXEC command copy flash tftp to send the compressed image back to the TFTP server.
- Uncompress the image at the TFTP server. (This cannot be done at a router.)
Step 8 Use the copy tftp flash privileged EXEC command at the router to retrieve the uncompressed image.
Step 9 Check the configuration register using the show version EXEC command. Set the router to boot from Flash memory (for example, 0x102).
Step 10 Use the write terminal privileged EXEC command to determine whether the router configuration includes the boot system flash global configuration command in the correct order with respect to the other boot system commands.
- Include the boot system flash command if it is missing. Confirm that the order of boot system commands is correct. Use the write memory command to save this change.
Step 11 Enter the reload privileged EXEC command to restart the box.
|
| Bad router hardware
|
Step 1 Troubleshoot router hardware as discussed earlier in this chapter.
|
Note The boot system global configuration commands are saved in the same order in which they were entered. The most recent entry goes to the bottom of the list.
Router Partially Boots from Flash and Display Shows Boot Prompt
Symptom: When booting a router from Flash memory, the boot process halts and the router displays the boot [router(boot)>] prompt. In addition, the router will not route, although the EXEC commands may appear to be operational. This symptom only applies to Cisco 2000, Cisco 2500, Cisco 3000, and Cisco 4000 routers.
Table 2-20 outlines possible causes and suggests actions when a router boots partially and displays the router(boot)> prompt on the console.
Table 2-20 : Router Startup: Router Boots Partially and Displays router(boot)> Prompt
| No system image in Flash memory
|
Step 1 Use the show flash EXEC command to determine whether an image exists in Flash memory.
Step 2 If no image exists, use the copy tftp flash privileged EXEC command to copy the system image from your TFTP server to the router's Flash memory. See the section "IP Default Gateway Configuration Notes," earlier in this chapter, for extra steps that you might have to perform.
Step 3 Enter the privileged EXEC command reload to boot the router.
|
| Misconfigured router (missing boot system flash global configuration command)
|
Step 1 Enter enabled mode.
Step 2 Use the write terminal privileged EXEC command to determine whether the active configuration includes an entry for the boot system flash global configuration command. Use the show configuration privileged EXEC command to determine if the boot system flash command is included in the configuration stored in NVRAM.
Step 3 Check the order of the boot system commands. For the recommended ordering, refer to the section "Using a Fault-Tolerant Boot Strategy" earlier in this chapter.
Step 4 Add the boot system flash command or reorder the boot system commands if necessary.
Step 5 Save the configuration change to NVRAM using the write memory privileged EXEC command.
|
| Misconfigured configuration register
|
Step 1 Check the configuration register setting; make sure it is set to boot from Flash memory (for example, 0x102).
Step 2 Refer to your hardware installation and maintenance publication for details regarding configuration register settings.
|
Router Fails to Boot from Flash Memory
Symptom: When booting a router from Flash memory, the boot process appears to complete, but the router does not route traffic or communicate with neighbors. The EXEC might or might not function. Table 2-21 outlines possible causes and suggests actions when a router fails to boot from Flash memory.
Table 2-21 : Router Startup: Router Fails to Boot from Flash Memory
| Incorrect or corrupted image; EXEC does not function
|
Step 1 Check the configuration register using the show version EXEC command. Set the register to boot from Flash memory (for example, 0x2102).
Step 2 Power-cycle the router.
Step 3 Within the first minute of booting, press the Break key to access the ROM monitor.
Step 4 At the ROM monitor prompt (
>
), enter o/r 0x1 to set the configuration register to boot from ROM.
Step 5 Enter i to reinitialize router, which causes the router to enter setup mode.
Step 6 Obtain the correct system image.
- (If necessary, contact your router technical support representative to determine which image is correct.)
Step 7 Once the correct image is identified, use the privileged EXEC command copy tftp flash at the router to retrieve the image.
Step 8 Check the configuration register using the show version EXEC command. Set the register to boot from Flash memory (for example, 0x102). For information about configuration register settings, refer to your hardware installation and maintenance documentation.
Step 9 Use the write terminal privileged EXEC command to determine whether the router configuration contains the boot system flash global configuration command.
- NOTE: Issuing the write memory command at this point on a Cisco 2500 series, Cisco 3000 series, Cisco 4000 series, or Cisco 7000 series will overwrite the configuration. Make sure you have a backup of your configuration file.
Step 10 Include the boot system flash command if it is not in the configuration. Be sure to use the write memory command after this change.
Step 11 Enter the privileged EXEC command reload to restart the router.
|
| Incorrect or corrupted image; EXEC functions
|
Step 1 Find a correct system image.
- (If necessary, contact your router technical support representative to determine which image is appropriate.)
Step 2 Once the correct image is identified, use the privileged EXEC command copy tftp flash at the router to retrieve the image.
Step 3 Check the configuration register using the show version EXEC command. Set the register to boot from Flash memory (for example, 0x102). For information about configuration register settings, refer to your hardware installation and maintenance documentation.
Step 4 Use the write terminal privileged EXEC command to determine whether the active configuration contains boot system flash global configuration command. Use the show configuration privileged EXEC command to determine if the boot system flash command is included in the configuration stored in NVRAM.
Step 5 Include the boot system flash command if it is not in the configuration. Be sure to use the write memory privileged EXEC command to save your modification after this change.
Step 6 Enter the reload privileged EXEC command to restart the router.
|
Terminal Connected to Unconfigured Access Server Is Unresponsive
Symptom: A terminal connected to the console port of an unconfigured Cisco access server (currently, the Cisco 2500 series access servers are the only Cisco devices that have an RJ-45-based console port) displays bootup banners and begins the Setup routine, but the user cannot input commands from the terminal keyboard. Table 2-22 describes possible causes and suggests actions for an unresponsive terminal connection to an unconfigured access server.
Table 2-22 : Router Startup: Unresponsive Terminal Connection to Unconfigured Access Server
| Flow control configured on the terminal conflicts with the EIA/TIA-232 control signals supported by the access server console port (RJ-45 to DB-25)
|
Step 1 Check if flow control is configured on your terminal.
Step 2 Disable all flow control on the terminal. With flow control enabled, the terminal will wait indefinitely for a CTS (Clear to Send) signal because the RJ-45 console port on the access server does not assert CTS. For information on how to check for and disable flow control on your specific terminal, consult the documentation provided by your terminal manufacturer.
Step 3 Alternately, you can "strap CTS high" by providing the proper voltage on the CTS signal lead to make the signal active. Find an unused signal that is known to be active and "strap," or short, CTS to it. The terminal sees CTS being asserted (indicating that the access server is ready to receive data) and allows input to be entered.
Step 4 On an already configured access server, another alternate solution is to connect your terminal to the auxiliary port of the access server. The auxiliary port, unlike the console port, does assert CTS and the terminal will therefore allow input. However, on a brand new access server with no configuration, this is not an alternative, because the bootup banners and Setup routine are seen only on the console port.
|
| Hardware problem
|
Step 1 Check all hardware for damage, including cabling (broken wire), adapters (loose pin), access server ports, and the terminal itself.
Step 2 Replace any hardware that is damaged or excessively worn.
|
Recovering a Lost Password
The following procedures describe the steps required to recover a lost login or enable password. The procedure differs depending on the platform and the software used, but in all cases, password recovery requires that the router be taken out of operation and powered down. Should you need to perform one of the following procedures, make certain that there are secondary systems that can temporarily serve the functions of the router undergoing the procedure. If this is not possible, advise all potential users and, if possible, perform the procedure during low use hours. Finally, be aware of the possible consequences of removing and reinserting a router on a functioning network.
Note Making a note of your password and storing it in a secure place is recommended.
All of the procedures for recovering lost passwords depend upon changing the configuration register of the router. Depending on the platform and software you are using, this will be done by reconfiguring the router software or by physically moving a jumper or dual inline package (DIP) switch on the router. Table 2-23 shows which platforms have configuration registers in software and which require that you change the jumper or DIP switch position to change the configuration register.
Table 2-23 : Configuration Registers for Specific Cisco Platforms and Software
| Cisco 2000 series
|
Yes
|
--
|
--
|
| Cisco 2500 series
|
Yes
|
--
|
--
|
| Cisco 3000 series
|
Yes
|
--
|
--
|
| Cisco 4000 series
|
Yes
|
--
|
--
|
| Cisco 7000 series running Software Release 9.17(4) or later (Flash/netboot) or Cisco IOS Release 10.0 or later (ROM)
|
Yes
|
--
|
--
|
| Cisco 7000 running Software Release 9.21 or earlier from ROM
|
--
|
Yes
|
--
|
| Cisco IGS running Software Release 9.1 or later
|
Yes
|
--
|
--
|
| Cisco IGS running software prior to Software Release 9.1
|
--
|
--
|
Yes
|
| Cisco CGS
|
--
|
Yes
|
--
|
| Cisco MGS
|
--
|
Yes
|
--
|
| Cisco AGS
|
--
|
Yes
|
--
|
| Cisco AGS+
|
--
|
Yes
|
--
|
Password Recovery Procedure: Platforms Running Current Cisco IOS Releases
The more recent platforms produced by Cisco run from Flash memory or are netbooted and have the capability to ignore the contents of NVRAM upon booting. (Cisco 7000 series routers that boot from Flash memory or netboot have this capability as well; a Cisco 7000 that boots from ROM has this capability if it is running Cisco IOS Release 10.0 or later.) Ignoring the contents of NVRAM permits you to bypass the configuration file (which contains the passwords) and gain complete access to the router. You can then recover the lost password(s) or configure new ones.
Note If your password is encrypted, you cannot recover it. You must configure a new password.
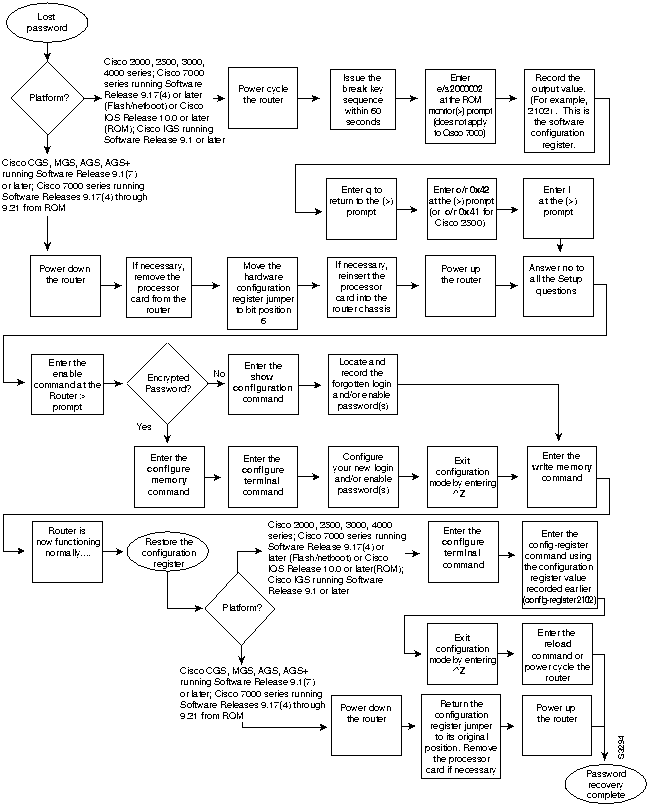
Figure 2-4 shows a flow chart describing the password recovery procedure for the following platforms:
- Cisco 2000, Cisco 2500, Cisco 3000, and Cisco 4000 series access servers and routers
- Cisco 7000 series routers running Software Release 9.17(4) and later from Flash/netboot or Cisco IOS Release 10.0 or later from ROM
- Cisco IGS routers running Software Release 9.1 or later
- Cisco CGS, MGS, AGS, and AGS+ routers running Software Release 9.1(7) or later
- Cisco 7000 series routers running Software Release 9.17(4) through 9.21 from ROM
Figure 2-4 illustrates the password recovery procedure for all of these platforms. Some of these platforms are configurable in software and do not require a hardware change. Others require that you physically change the position of the configuration register jumper on the processor card. Figure 2-4 shows diverging paths, when necessary, to take you through the steps required for the platform and software with which you are working. Refer to Table 2-23 to determine if the platform with which you are working is configurable in the software, or if it requires you to physically move the jumper.
The following procedure describes the password recovery process for the following platforms only:
- Cisco 2000, Cisco 2500, Cisco 3000, and Cisco 4000 series routers
- Cisco 7000 series routers running Software Release 9.17(4) or later (Flash memory or netboot) or Cisco IOS Release 10.0 or later from ROM
- Cisco IGS Running Software Release 9.1 or later
For the platforms listed, be certain to follow the path shown in the flowchart (see Figure 2-4) labeled "Cisco 2000, 2500, 3000, 4000 series; Cisco 7000 series running Software Release 9.17(4) or later (Flash/netboot) or Cisco IOS Release 10.0 or later (ROM); IGS running Software Release 9.1 or later."
For the step-by-step password recovery sequence for other platforms, see one of the following sections: "Password Recovery Procedure: Platforms Running Recent Software Releases," "Password Recovery Procedure: Platforms Running Earlier Software Releases," "Password Recovery Procedure: IGS Running Software Prior to Software Release 9.1," or "Password Recovery Procedure: Cisco 500-CS Communication Server."
Note To complete this procedure, you must have a terminal or a personal computer (running terminal emulation software) connected to the console port of the router. In addition, you should know the key sequence necessary to issue the break command from your terminal.
Following is the password-recovery procedure for Cisco platforms running current Cisco IOS software:
Step 1 Power cycle the router. (This consists of turning off the power to the router and turning it back on again.)
Step 2 Issue the break key sequence for your terminal or terminal emulation software within 60 seconds of turning on the power.
- The ROM monitor (>) prompt will appear.
Step 3 Enter the command, e/s 2000002. (For Cisco 7000 series routers, enter e/s XXXXXXXX.) This command examines the short (16 bit) memory location for the software configuration register.
- Record the output resulting from this command. This is the software configuration register value.
Note In this procedure, 2102 is used as an example software configuration register value.
Step 4 Enter the q (quit) command to return to the ROM monitor (>) prompt.
Step 5 Enter the o/r 0x42 command. (For a Cisco 2500, use the command 0x041.) The value 42 (or 41 on a Cisco 2500) sets the software configuration register bit to position 6, which allows the router to ignore the contents of NVRAM when booting. (Be sure to enter 0x followed by the configuration register value.)
Step 6 Enter the i (initialize) command at the ROM monitor (>) prompt. The router will reboot.
Step 7 Answer no to all of the Setup questions.
Step 8 Enter the enable EXEC command at the Router> prompt.
Step 9 If your password is clear text (is not encrypted), proceed to Step 13.
- or
- If your password is encrypted, continue with Step 10.
Step 10 If your password is encrypted, enter the configure memory privileged EXEC command. This writes the stored configuration into running memory.
Step 11 Enter the configure terminal privileged EXEC command to enter router configuration mode.
Step 12 If you lost the enable password, use the enable-password global configuration command to configure a new password and press ^Z to exit configuration mode.
- or
- If you lost the login password, configure the console line using the login and password line configuration commands. Enter ^Z to exit configuration mode and proceed to Step 15.
Step 13 If your password is clear text (is not encrypted), enter the show configuration privileged EXEC command to view the current configuration.
Step 14 If you lost the enable password, locate the enable-password global configuration command entry in the configuration and record the password.
- or
- If you lost the login password, find the configuration entries for the console line and record the password indicated by the password line configuration command.
Step 15 Issue the write memory privileged EXEC command to write the configuration into running memory.
 Caution Issuing the write memory command at this point on a Cisco 2500, Cisco 3000, or Cisco 4000 will overwrite the configuration. Make certain you have a backup of your configuration file.
Caution Issuing the write memory command at this point on a Cisco 2500, Cisco 3000, or Cisco 4000 will overwrite the configuration. Make certain you have a backup of your configuration file.
Step 16 The router is now fully functional, and you can use your recovered or reconfigured password(s) as usual.
Note Restore the software configuration register to its original value as soon as possible. If it is not returned to the value you noted in Step 3, the router will always ignore the contents of NVRAM and enter the Setup routine upon booting. Continue with Step 17 to return the software configuration register to its original value.
Step 17 In privileged EXEC mode, enter router configuration mode using the configure terminal privileged EXEC command.
Step 18 Change the software configuration register to its original value using the config-register global configuration command. You must enter 0x and then the software configuration register value that you recorded in Step 3. Using the example value of 2102, the command would be config-register 0x2102.
Step 19 Exit from router configuration mode by entering ^Z.
- The next time the router is power cycled or restarted with the reload privileged EXEC command, the bootup process will proceed as normal. Use your new or recovered password to gain access to the router after it reboots.
Figure 2-4 : Password Recovery: Platforms Running Current Cisco IOS Releases and Recent Software Releases
Password Recovery Procedure: Platforms Running Recent Software Releases
The Cisco CGS, MGS, AGS, and AGS+ platforms, and Cisco 7000 series routers running software prior to Cisco IOS Release 10.0 from ROM, all have their configuration registers in hardware, so you must physically change the position of the configuration register jumper during the password recovery process. It may be necessary to remove the processor card from the router chassis in order to access the hardware configuration register jumper. Consult your hardware documentation for detailed instructions on removing and inserting the processor card from the router chassis if necessary.
Moving the hardware configuration register jumper to bit position 6 allows the router to ignore the contents of NVRAM while booting. This permits you to bypass the configuration file (and therefore the passwords) and gain complete access to the router. You can then recover the lost password(s) or configure new ones.
Note If your password is encrypted, you cannot recover it. You must configure a new password.
Figure 2-4 shows a flow chart describing the password recovery procedure for the following platforms:
- Cisco 2000, Cisco 2500, Cisco 3000, and Cisco 4000 series access servers and routers
- Cisco 7000 series routers running Software Release 9.17(4) and later from Flash memory/netboot
- or
- Cisco 7000 series routers running Cisco IOS Release 10.0 or later from ROM
- Cisco IGS routers running Software Release 9.1 or later
- Cisco CGS, MGS, AGS, and AGS+ routers running Software Release 9.1(7) or later
- Cisco 7000 series routers running Software Release 9.17(4) through 9.21 from ROM
Figure 2-4 illustrates the password recovery procedure for all of these platforms. Some of these platforms are configurable in software and do not require a hardware change. Others require that you physically change the position of the configuration register jumper on the processor card. Figure 2-4 takes you through the steps required for the platform and software with which you are working, and shows diverging paths when necessary to account for platform-specific requirements. Refer to Table 2-23 to determine if the platform on which you are working is configurable in the software, or if it requires you to physically move the jumper.
The following textual procedure describes the password recovery process for the following platforms only:
- Cisco CGS, MGS, AGS, and AGS+ routers running Software Release 9.1(7) and later
- Cisco 7000 series routers running Software Release 9.17(4) through 9.21 from ROM
For these platforms, follow the path shown in the flowchart (see Figure 2-4) labeled "Cisco CGS, MGS, AGS, AGS+ running Software Release 9.1(7) or later; Cisco 7000 series running Software Release 9.17(4) through 9.21 from ROM."
For the step-by-step password recovery sequence for other platforms, see one of the following sections: "Password Recovery Procedure: Platforms Running Current Cisco IOS Releases," "Password Recovery Procedure: Platforms Running Earlier Software Releases," "Password Recovery Procedure: IGS Running Software Prior to Software Release 9.1," or "Password Recovery Procedure: Cisco 500-CS Communication Server."
Note To complete this procedure, you must have a terminal or a personal computer (running terminal emulation software) connected to the console port of the router.
Following is the password-recovery procedure for Cisco platforms running recent software releases:
Step 1 Power down the router.
Step 2 Change the hardware configuration register by moving the jumper from bit position 0 (zero) or 1 to bit position 6.
- This will force the router to ignore the contents of NVRAM, and therefore the configuration file, after it loads the operating system. Note the original position of the jumper.
Note To move the hardware configuration register jumper, you might need to remove the processor card from the router chassis. This is the case with the Route Processor (RP) card in Cisco 7000 series routers. Consult your hardware documentation for complete instructions on removing and inserting the processor card. If you had to remove the processor card, reinsert it before continuing.
Step 3 Power up the router.
- The router will boot but will ignore the contents of NVRAM and enter the Setup routine.
Step 4 Answer no to all of the Setup questions.
- The Router> prompt appears.
Step 5 Enter the enable EXEC command.
Step 6 If the password is clear text (is not encrypted), go to Step 10. If the password is encrypted, continue with Step 7.
Step 7 If the password is encrypted, enter the configure memory privileged EXEC command. This writes the stored configuration into running memory.
Step 8 Enter the configure terminal privileged EXEC command to enter router configuration mode.
Step 9 If you have lost the enable password, use the enable-password global configuration command to configure a new password. If you have lost the login password, configure the console line with a new login password using the login and password line configuration commands. Press ^Z to exit configuration mode. Proceed to Step 12.
Step 10 If your password is clear text (is not encrypted), enter the show configuration privileged EXEC command.
Step 11 If you have lost the enable password, locate the enable-password global configuration command entry and record the password. If you have lost the login password, find the configuration entries for the console line and record the password indicated by the password line configuration command.
Step 12 Issue the write memory privileged EXEC command to write the configuration into running memory.
Step 13 The router is now fully functional and you can use your recovered or reconfigured password(s) as usual.
Note Return the hardware configuration register jumper to its original position as soon as possible. If the jumper is not returned to the bit position you noted in Step 2, the router will always ignore the contents of NVRAM and enter the Setup routine upon booting. Continue with Step 14 to return the jumper to its original position.
Step 14 Power down the router.
Step 15 Move the hardware configuration register jumper from bit position 6 to its original position (the position you noted in Step 2).
- It might be necessary to remove the processor card to gain access to the jumper. Consult your hardware documentation for complete instructions on removing and inserting the processor card if necessary. If you had to remove the processor card, reinsert it before continuing.
Step 16 Power up the router. Use your new or recovered password to gain access to the router.
Password Recovery Procedure: Platforms Running Earlier Software Releases
Cisco CGS, MGS, AGS, and AGS+ platforms, and Cisco 7000 series routers running software prior to Cisco IOS Release 10.0 from ROM, all have their configuration registers in the hardware, so you must physically change the position of the configuration register jumper during the password recovery process. It might be necessary to remove the processor card from the router chassis in order to access the hardware configuration register jumper. Consult your hardware documentation for detailed instructions on removing and inserting the processor card from the router chassis if necessary.
Note It is important to remember that if your password is encrypted, you cannot recover it. You must configure a new password.
Figure 2-5 shows a flowchart that describes the password recovery procedure for the following platforms:
- CGS, MGS, AGS, and AGS+ routers running Software Release 9.1(6) and earlier
- Cisco 7000 series routers running Software Release 9.17(3) and earlier from ROM
The step-by-step procedure that follows and the password recovery flow chart shown in Figure 2-5 apply only to the indicated platforms running the indicated software. There is another procedure for recovering a password on these platforms if they are running more recent software. See the previous section, "Password Recovery Procedure: Platforms Running Recent Software Releases."
Note To complete this procedure, you must have a terminal or a personal computer (running terminal emulation software) connected to the console port of the router.
Following is the password-recovery procedure for Cisco platforms running earlier software releases:
Step 1 Power down the router.
Step 2 Change the hardware configuration register by moving the jumper from bit position 0 (zero) or 1 to bit position 15.
- Note the original position of the jumper.
Note To move the hardware configuration register jumper, you might need to remove the processor card from the router chassis. This is the case with the Route Processor (RP) card in Cisco 7000 series routers. Consult your hardware documentation for complete instructions on removing and inserting the processor card. If you had to remove the processor card, reinsert it before continuing.
Step 3 Power up the router. The ROM monitor (>) prompt appears.
Step 4 Enter the b (bootstrap) command at the (>) prompt.
Step 5 Press the Return key until the Test-System> prompt appears.
Step 6 Enter privileged mode by issuing the enable EXEC command.
Step 7 If the password is clear text (is not encrypted), go to Step 12.
- or
- If the password is encrypted, continue with Step 8.
Step 8 If the password is encrypted, enter the configure memory privileged EXEC command.
- This writes the stored configuration into running memory.
Step 9 Enter the configure terminal privileged EXEC command to enter router configuration mode.
Step 10 If you have lost the enable password, use the enable-password global configuration command to configure a new password and press ^Z to exit configuration mode.
- or
- If you have lost the login password, configure the console line with a new password using the login and password line configuration commands. Press ^Z to exit configuration mode.
Step 11 Issue the write memory privileged EXEC command to write the configuration into running memory. Proceed to Step 14.
Step 12 If your password is clear text (is not encrypted), enter the show configuration privileged EXEC command.
Step 13 If you have lost the enable password, locate the enable-password global configuration command entry in the configuration and record the password.
- or
- If you have lost the login password, find the configuration entries for the console line and record the password indicated by the password line configuration command. Do not make configuration changes or use the write memory command at this time.
Step 14 Power down the router.
Step 15 Remove the processor card and move the hardware configuration register jumper from bit position 15 to its original position (the position you noted in Step 2).
Step 16 Power up the router. Use your new or recovered password to gain access to the router.
Figure 2-5 : Password Recovery: Platforms Running Earlier Software Releases
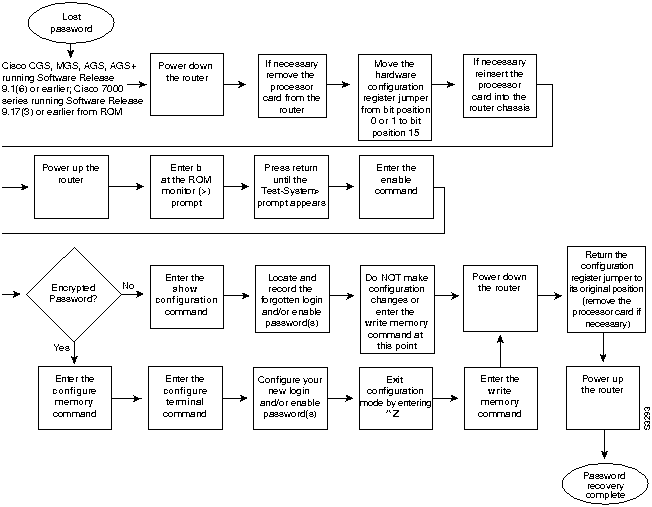
Password Recovery Procedure: IGS Running Software Prior to Software Release 9.1
Cisco IGS routers have a bank of DIP switches located on the rear panel. These DIP switches are used to set the hardware configuration register and must used in the password recovery process if the router is running system software prior to Software Release 9.1.
Figure 2-6 shows the password recovery procedure for the Cisco IGS running software prior to Software Release 9.1. There is another procedure for the IGS platform if it is running Software Release 9.1 or later. See the section, "Password Recovery Procedure: Platforms Running Current Cisco IOS Releases."
Note It is important to note that if your password is encrypted, you cannot recover it. You must configure a new password.
Note To complete this procedure, you must have a terminal or a personal computer (running terminal emulation software) connected to the console port of the router.
Following is the password-recovery procedure for IGS routers running software prior to Software Release 9.1:
Step 1 Power down the router.
Step 2 Record the settings of the DIP switches located on the rear panel of the router. You will need to return these switches to their original positions after you have recovered your password.
Step 3 Set switch number 7 to the ON position (down).
Step 4 Set switches 0--3 to the OFF position (up).
Step 5 Power up the router.
- The router will boot up, and the terminal will display the ROM monitor (>) prompt.
Step 6 Enter the b (bootstrap) command at the (>) prompt.
Step 7 Press the Return key until the Test-System> prompt appears.
Step 8 Enter the enable privileged EXEC command at the Test-System> prompt.
Step 9 If the password is clear text (is not encrypted), go to Step 14.
- or
- If the password is encrypted, continue with Step 10.
Step 10 If the password is encrypted, enter the configure memory privileged EXEC command. This writes the stored configuration into running memory.
Step 11 Enter the configure terminal privileged EXEC command to enter router configuration mode.
Step 12 If you have lost the enable password, use the enable-password global configuration command to configure a new password and press ^Z to exit configuration mode.
- or
- If you have lost the login password, configure a new password on the console line using the login and password line configuration commands. Press ^Z to exit configuration mode.
Step 13 Enter the write memory privileged EXEC command to write the configuration changes into stored memory. Proceed to Step 16.
Step 14 If your password is clear text (is not encrypted), enter the show configuration privileged EXEC command.
Step 15 If you have lost the enable password, locate the enable-password global configuration command entry in the configuration and record the password.
- or
- If you have lost the login password, find the configuration entries for the console line and record the password indicated by the password line configuration command. Do not make configuration changes or issue the write memory command at this time.
Step 16 Power down the router.
Step 17 Return the hardware configuration register DIP switches located on the back panel of the router to their original settings (the settings you noted in Step 2).
Step 18 Power up the router. Use your new or recovered password to gain access to the router.
Figure 2-6 : Password Recovery: IGS Running Software Release Prior to 9.1
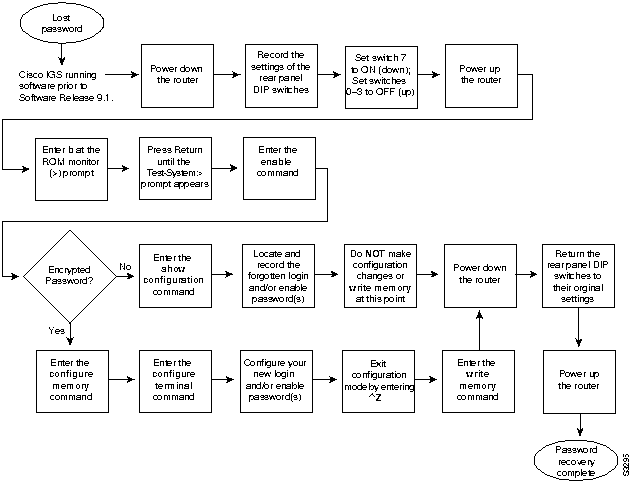
Password Recovery Procedure: Cisco 500-CS Communication Server
Lost passwords cannot be recovered from Cisco 500-CS communication servers. The only way to recover from a lost password is to return the communication server to its factory default configuration using the reset button located on the top of the case.
The following procedure describes how to restore the Cisco 500-CS to its default configuration:
Step 1 Power down the communication server.
Step 2 Press and hold down the reset button on the top of the case while turning on the power to the communication server.
Step 3 The 500-CS is returned to its factory default configuration.
- You must reconfigure the communication server. For information on configuring a Cisco 500-CS communication server, consult the Access and Communication Servers Configuration Guide and the Access and Configuration Servers Command Reference publications.
Copyright 1988-1996 © Cisco Systems Inc.
![]()
![]()



![]()



![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()